How the passwords are hacked? Tricks to create a strong password
Passwords were first used in the early 1960s at the Massachusetts Institute of Technology (MIT) on the Compatible Time-Sharing System (CTSS). Users were required to enter a password to access the system.
Passwords are like the locks that protect our online accounts, such as email, social media, and bank accounts. They are the first line of defense against cyber threats. However, even though passwords are so important, many people still use simple and easy-to-guess passwords, which makes it easy for hackers and thieves to access their accounts and steal their information.
In this blog we will discuss about weak passwords and the tricks to create a strong password.
Most commonly used PIN number:
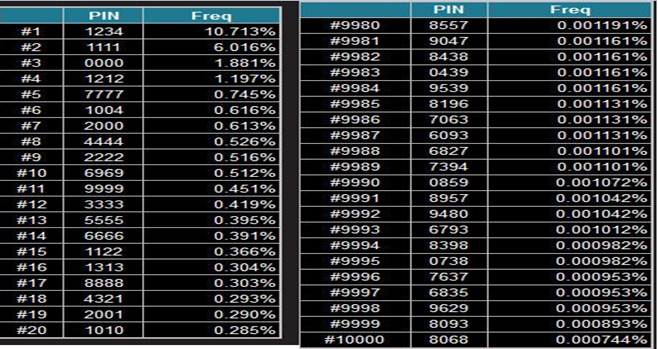
The most commonly used PIN number is 1234, which is very easy for anyone, even those with limited computer knowledge, to guess. If users are allowed to repeat numbers in their PIN, there are 10,000 possible combinations for a four-digit PIN (10 options for each digit). However, if repeats are not allowed, there are only 5,040 possible combinations.
Using Birth year as Password:
Unfortunately, many people use PINs that may seem secure but are actually weak and easy to guess. For example, some individuals use their birth year (e.g., 1992, 1991, 1983) as their PIN. Others combine the year with their birth month, like 0492 for April 1992 or 1291 for December 1991. They are very easy for hackers to guess and access.
Revealing PIN Due to Traces of Touch Pattern on Screens:
In addition to using weak PINs, some people unintentionally reveal their PINs by leaving traces of their touch patterns on screens. For example, on a phone or garage PIN pad, frequently pressed keys may show visible patterns. With enough observation and patience, someone might be able to guess the PIN based on these patterns.
It's essential for users to be aware of the importance of using strong, unique PINs to protect their accounts and personal information from unauthorized access. Image attached for reference is a data for most commonly used passwords in 2012:
2-Lowercase Character Password:
If we take ab 2 lowercase characters as an example the only 4 possible passwords will be ab, ba, aa, and bb. Even a child can detect this.
3-Lowercase character password:
If we take abc as an example there will be more possibilities. It will give abc, aaa, bbb, ccc, abb, aab, acb, bbc, bac, cab, ccb, cbb, caa, cca, cba, bcc, aac, thus making it harder to guess. But these passwords are still not strong and with time can be cracked.
How to Create more Stronger Passwords:
It is good to use an eight character password using uppercase and lowercase letters and numbers from 0-9. It will lead to give a very complex password that will take a long time for any brute force attack to crack it.
Password Recovery Tool:
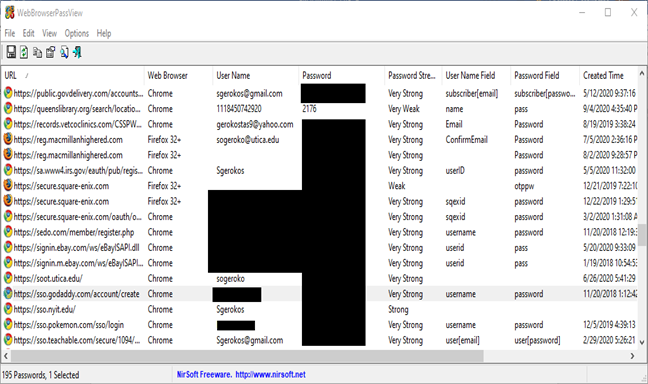
A straightforward password recovery tool can potentially compromise sensitive information in an unethical manner. For research purposes we used the tool named "WebBrowserPassView” . It was utilized on a system to retrieve passwords of the current system from web browsers.
This program successfully recovered all passwords, including associated usernames and URL links to various websites, such as Queens Library and Utica.edu. Interestingly, the tool also provided information about the strength of each password, classifying the Queens Library password as very weak due to its four-digit nature and the Utica.edu password as highly secure.
The below given figure shows the result when we used “WebBrowserPassView” to retrieve passwords.
How to make a strong password and check its strength online:
There are many websites that check the strength of a password. For example I use one uppercase letter 11 lower case characters one special character and three numbers with a total of 16 characters password and checked it online. It is ranked as an excellent password and is 100% strong. This password is not the part of 10,000 passwords so it will not show up on the list of used passwords online. This shows how a strong password can be made with minimal effort and the password is easily memorized by the user.
Since it does not exist on the list therefore the hacker will not be able to decrypt it easily because most hackers use online databases of passwords to commit a brute force attack.
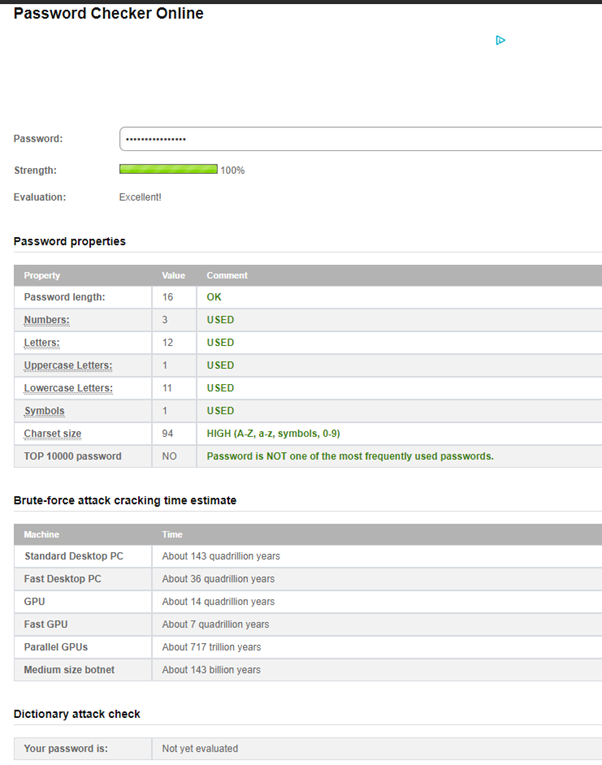
This above image is the result of password checker online where I checked the strength of my password.
Conclusion:
The evolution of technology has brought unprecedented convenience, but it has also opened the door to increasingly sophisticated cyber threats. From weak passwords and password reuse to phishing attacks and data breaches, there are numerous entry points for hackers to exploit.
By adopting strong and unique passwords, utilizing two-factor authentication, staying vigilant against phishing attempts, and staying informed about potential data breaches, we can significantly reduce the risk of falling victim to password hacking.
Stay Tuned
The best articles, links, and news delivered once a week to your inbox.
