How to detect a Phishing Email? Cyber Security tricks
Phishing emails are fraudulent messages sent by cybercriminals with the intent to deceive recipients into revealing sensitive information, such as usernames, passwords, credit card details, or other personal information. These emails often appear to be from a legitimate source, like a well-known company, government agency, or financial institution, but they are designed to trick you into clicking on malicious links or downloading harmful attachments.
Phishing emails are typically sent en masse. Attackers use automated tools to distribute these messages to a large number of email addresses, hoping that even a small percentage of recipients will fall for the scam.
How to Verify a Phishing Email:
There are various methods that help you to verify that an email is coming from a legitimate source or not. Some of these are discussed below with example:
Email about Failed Login:
The most evident way to spot a fake email is if the user receives a notification of failed login attempts when they haven't tried logging in at all. Additionally, checking the destination of any links in the email by right-clicking and copying the link address to a separate document can help determine if the link is legitimate or not, especially if it doesn't lead to the expected website like Citi Bank.
The below given picture is attached for the reference.
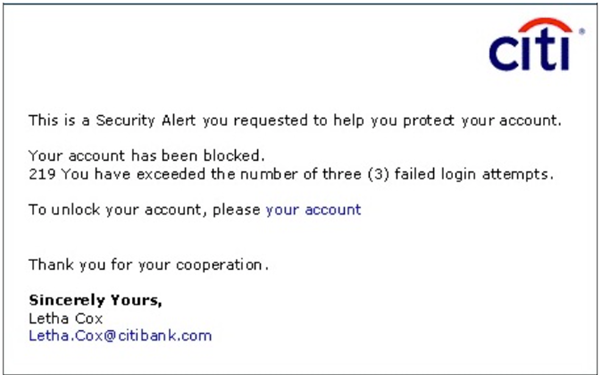
Unusual Account Number:
Another red flag is the presence of an unusual account number, like "219" in this case. Typically, banks request the last four digits of an account number, not three, and they don't usually send these numbers in emails. If it's meant to be an error number, it should be clearly labeled as "error 219," making the email even more suspicious. It's unlikely that "219" is a CVC number because users can verify this without logging into their account.
Call to the Corresponding Channel to Verify Email:
To be certain about the email's authenticity, users can call their bank to inquire if their account is locked and explain the situation. Most banks have dedicated channels to report and forward suspicious emails, and they will be glad to assist in verifying the email's legitimacy.
Stay Calm and Think Before Clicking Any Link;
To prevent falling victim to such scams, users should stay calm and ask themselves questions about the email's authenticity before clicking any links or taking action. Being vigilant and cautious is essential in safeguarding personal information and avoiding phishing attempts.
Spear phishing Email:
Spear phishing is a more targeted and sophisticated form of phishing email. In contrast to regular phishing emails that are sent en masse to a large number of recipients, spear phishing emails are carefully tailored and personalized to deceive specific individuals or a select group of targets. The term "spear" in spear phishing refers to the focused and precise nature of the attack, like using a spear to target a specific fish in a pond.
Spoofed Identities:
The sender's email address and display name may be carefully crafted to appear as though the email is coming from a trusted individual or a legitimate source that the target recognizes.
How to Verify a Spear Phishing Email:
The following figure shows a spear phishing email. In this email there are a few things a user can do to verify it is false. We may try to explain using the below given image as reference.
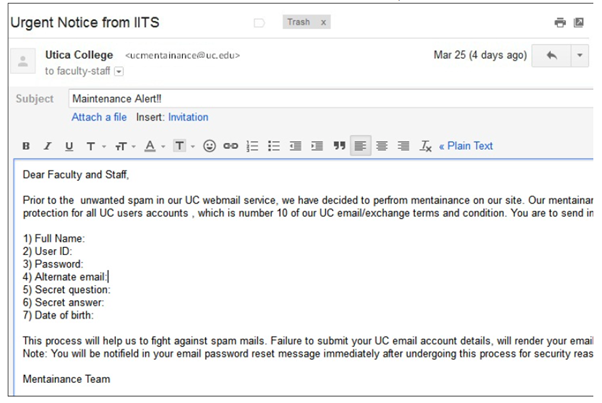
Sender's Email Address:
It's quite evident that this email is suspicious and likely fake, mainly because of the sender's email address. Legitimate emails from utica.edu should have "@utica.edu" in the sender's address, but this one shows "uc.edu," which immediately raises red flags.
Requesting a lot of Data:
Moreover, the email requests a vast amount of personal information, including Full Name, User ID, Password, Alternate email, Security question, Secret question, Secret answer, and Date of birth. Reputable organizations and maintenance processes would never ask for such sensitive information via email. It's highly unusual for any legitimate organization to request all this data at once through email.
Threats of being Locked out of Account:
Another questionable element is the threat of being locked out of the account. In case of a legitimate issue, users can usually resolve it with a simple phone call to the organization's support team. They would not require users to follow instructions in an email to avoid being locked out.
Email's Header and IP Address:
For those with advanced technical knowledge, examining the email's header and checking the IP address can provide further clues about the email's authenticity. However, for the average user, it's essential to recognize the obvious signs of suspicious activity and avoid responding to such emails altogether.
Conclusion;
Always remember to be cautious when receiving emails from unfamiliar sources or those requesting sensitive information. Never click on suspicious links or download attachments from unknown senders, as these could lead to the installation of malware on your device.
One of the essential aspects of avoiding phishing attacks is staying informed about the latest tactics employed by cybercriminals. Regularly educate yourself and your family members or colleagues about phishing techniques, as awareness is a powerful weapon in the fight against cyber threats.
Stay Tuned
The best articles, links, and news delivered once a week to your inbox.
