How to Hide a File inside another File Using Steganography Tools
In modern times, steganography allows people to conceal critical information within files or images. Although cryptography may be more widely known and used for securing data, steganography still holds significant relevance in various scenarios. It serves a wide range of purposes, from innocent endeavors like children's games and secret messages among friends, to more serious applications like military communication between soldiers or secure transmissions within government branches. Unfortunately, steganography can also be employed by hackers for malicious purposes, such as hiding viruses
History of Steganography:
Steganography, an ancient art of concealing messages or data, has evolved over time and continues to be utilized in the digital age for various purposes. Historically, people employed ingenious methods like invisible ink to hide information. One of the earliest recorded instances of steganography can be found in Herodotus' Histories. It tells the story of Histiaeus, the ruler of Miletus, who planned a revolt against the Persians. He used a clever technique by having a slave shave their head, tattoo a message on their scalp, let the hair regrow, and then sent the slave to deliver the hidden message to his son-in-law, Aristagoras, for the covert planning of the rebellion.
Encryption using Null Cipher:
Below given image illustrates an example of a null cipher, an encryption technique widely used to conceal hidden messages within a paragraph, making it seemingly inconspicuous to the naked eye. Upon closer examination, one can identify the hidden message by extracting the first capital letter of each sentence and combining them to form a coherent sentence.

Hiding a File inside Another File:
The purpose of this tutorial is to familiarize oneself with the steganography tool S-Tools. Through this tutorial one will learn to properly hide a file inside another file and to reveal information from a file. One will also understand how the file can be corrupted and loose the data.
Program S-Tools:
First, you need to download and install S-tools on your computer. You can find the software on reputable websites that distribute steganography tools. After installing the software, open it by clicking on the S-tools icon or accessing it from the Start menu.
You can see the program S-tools running in the given image.

Hiding in a .gif File in S-tools:
In S-tools, the carrier image is the picture or file where you want to hide your .gif file. Click on the "Open" or "Select File" button to choose the carrier image. It can be a JPEG, PNG, or any other image format supported by S-tools.
Once the carrier image is selected, go to the "Embed File" or "Hide File" option in the S-tools menu. Choose the .gif file you want to hide and click "Open" or "OK" to embed it into the carrier image
Hidden Data Image:
You can see a hidden data image in the image below it was made with a passphrase Password and Triple DES algorithm.
Extracting the Hidden File from S-tools:
Once the carrier image is loaded, go to the "Extract File" or "Unhide File" option in the S-tools menu. This option allows you to retrieve the hidden file from the carrier image.
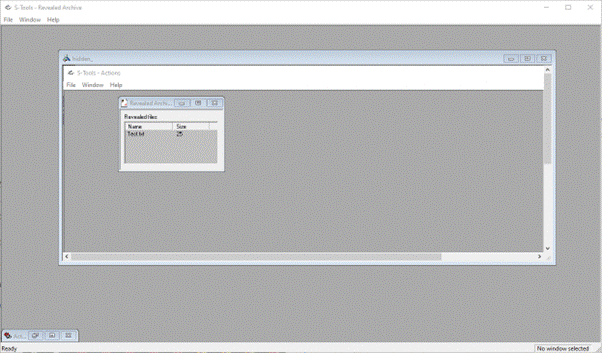
In the above image, the hidden file was initially embedded in a .bmp file, and S-tools was used to extract it successfully. However, the user decided to convert the .bmp file to .jpeg format using Paint, and then revert it back to .bmp using Paint again. Unfortunately, during this conversion process, the text file containing the hidden message was either lost or modified, and the hidden information could not be retrieved intact.
Steganography in Black Hat Hacking
A Black hat hacker might choose to use steganography alone, without cryptography, when embedding malware into a file using S-tools. By doing so, the hacker aims to conceal the presence of the malicious code within the file, making it harder for antivirus software or security measures to detect it. The absence of encryption means that the hidden data is not protected by a passphrase, but the hacker relies on the fact that steganography itself is difficult to detect unless someone is already aware of the hidden information or suspects its presence and uses a tool like S-tools to check for it. However, there is still a risk of antivirus software identifying the file as infected and removing it before any damage can be done.
Conclusion:
An individual passing off a secret message might prefer to use both steganography and cryptography. By combining these techniques, the person can ensure that the information remains securely hidden within the file, and only those with the correct passphrase can access and decrypt it. This added layer of encryption provides an extra level of protection in case someone discovers the presence of hidden data, as the information would be unintelligible without the passphrase.
Stay Tuned
The best articles, links, and news delivered once a week to your inbox.
