How To Use Wireshark A Packet Sniffing Tool On Kali Linux
Wireshark is a powerful network protocol analyzer that allows you to capture and analyze network traffic. Whether you are a network administrator, a cyber security professional, or simply curious about how data flows through networks, Wireshark is an essential tool for understanding and troubleshooting network communications.
Introduction to Wireshark:
With Wireshark, you can capture packets from a network connection and gain insights into the network traffic. This tool is particularly useful for troubleshooting network issues, identifying performance bottlenecks, and ensuring the security of your network.
While Wireshark itself is a legitimate and powerful tool, it's important to note that unethical individuals, commonly referred to as black hat hackers, can misuse it when connected to open networks. They may attempt to intercept sensitive information like passwords, usernames, credit card details, or any other data transmitted over the network.
Welcome To Wireshark:
The above picture shows Kali Linux packet sniffing tool WireShark.
Open the FTP Screen:
Now open the file ftp_transfer.pcap in WireShark.
FTP Filter in Wireshark:
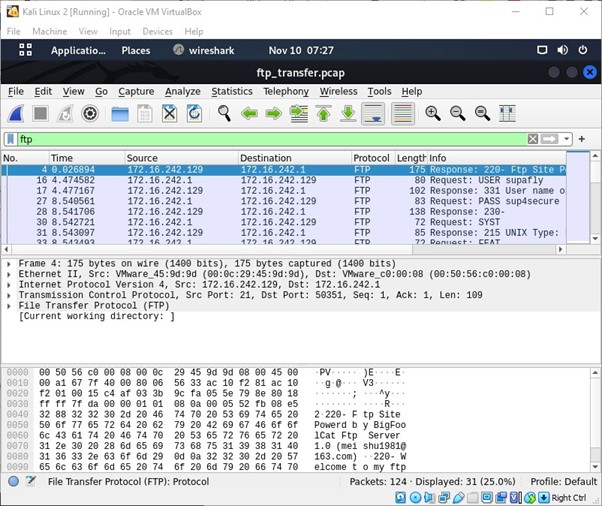
The above picture shows the filter FTP applied to WireShark this help’s filter only FTP related traffic in WireShark. The filter that was typed in “ftp” as shown in the Figure.
Packet Numbers:
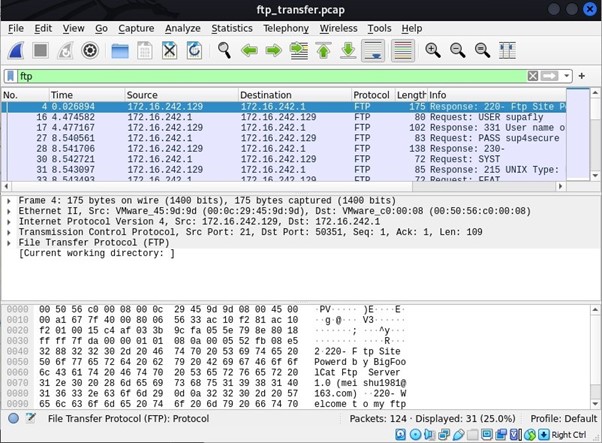
In the above picture you can see the packet numbers which are number 16 for username, and 27 for password these where captured in this file. The Username being superfly, the Password being sup4secure.
Saving a packet using command follow stream:
You can see a packet by opening it and can save it by using command follow stream.
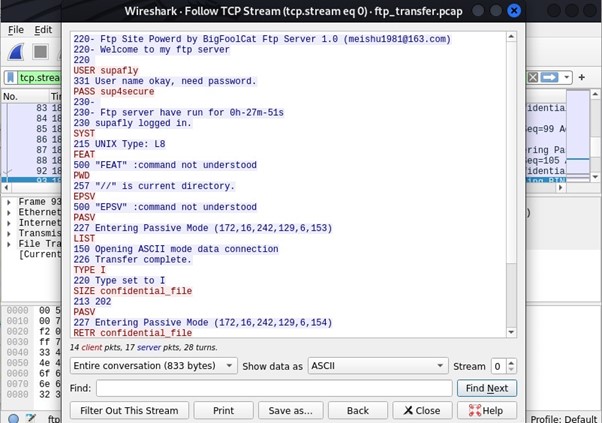
In this case we are showing for packet 93.
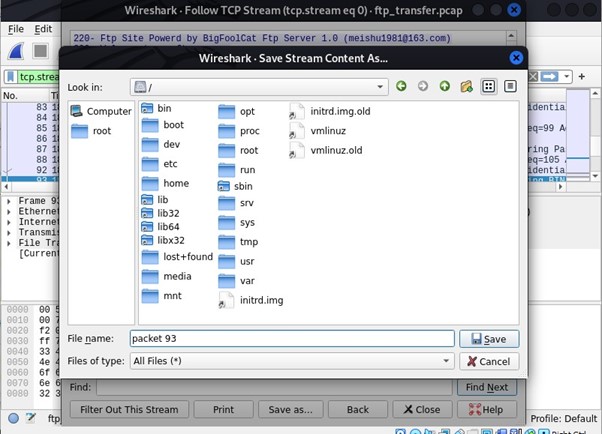
You can save the file as shown below.
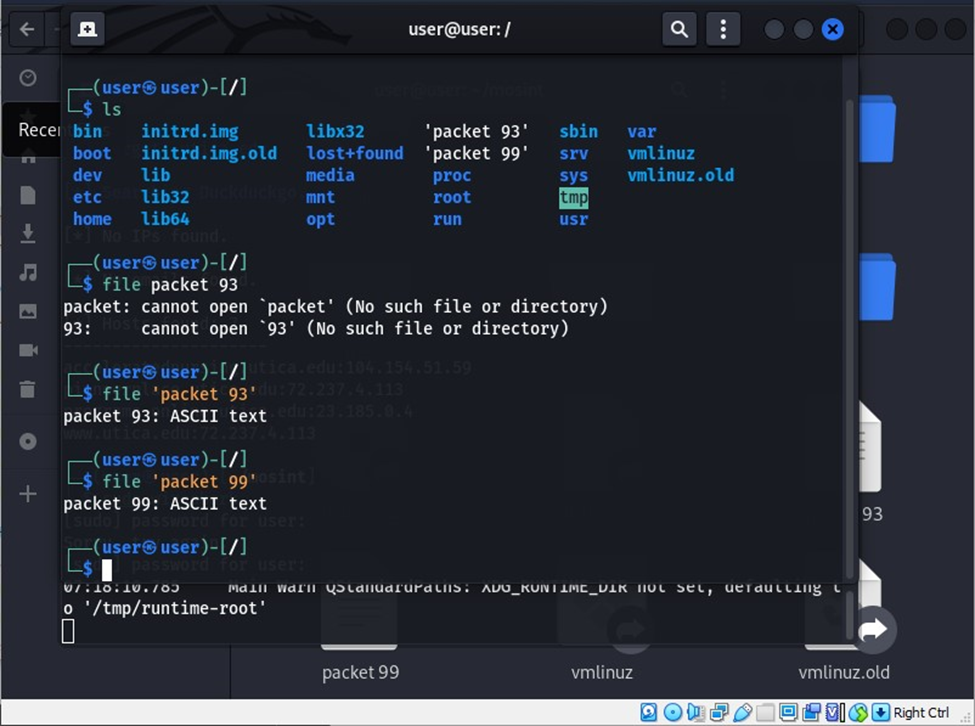
Using command “file” to identify files:
You can use the command “file” to identify files. The files are ASCII text files.
The following image depicts the steps for adding the packet file in .ascii format on a host computer, with the intention of attempting to open it in the Windows operating system.
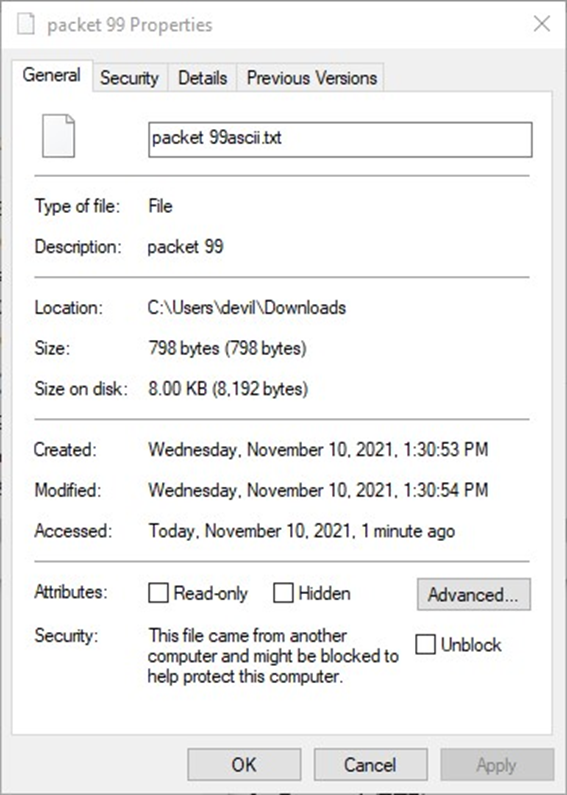
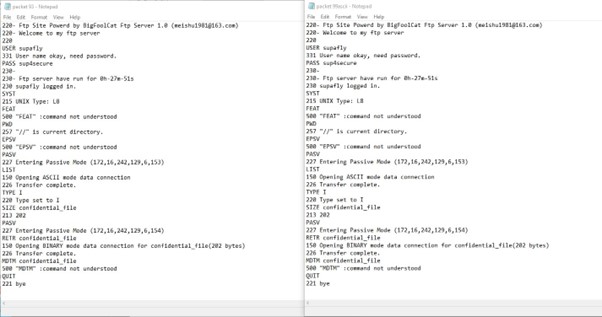
Opening .ascii files in windows:
You can open both files in notepad on windows. The files cannot be opened if the .ascii extension is not added in the end as this is required in windows. As seen in the figure the files both opened when the extension was added.
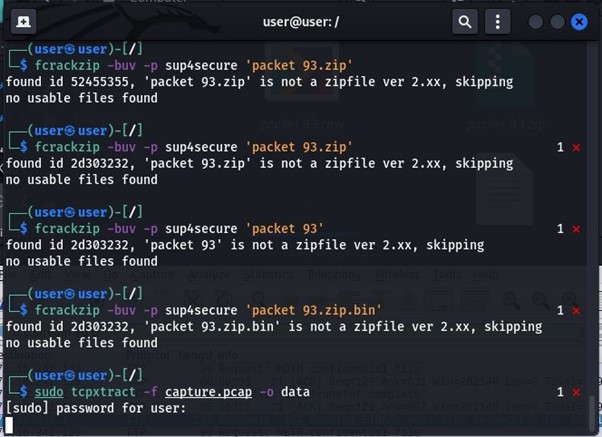
Extract the file from pcap file:
The following image shows tcpxtract being used on the entire pcap file to extract the file. This is another method to extract data from a saved packet.
Conclusion
In conclusion, this tutorial has provided you with a comprehensive introduction to Wireshark, a powerful network protocol analyzer. We've covered the basics of capturing network traffic, analyzing packets, and gaining valuable insights into network communications.
Stay Tuned
The best articles, links, and news delivered once a week to your inbox.
