How to Use Wireshark to Capture Packets and View Network Data
Introduction to Wireshark and Network Packets:
Wireshark is a powerful tool used to capture and analyze network packets, which are essential data units exchanged between computers and network devices. These packets facilitate communication and data exchange within a network.
Enhancing Network Security with Wireshark:
Wireshark plays a crucial role in network security by allowing security professionals to closely examine packets, identify their origins and destinations, and detect potential malicious activities. Its proactive approach helps prevent security breaches and the spread of harmful content.
The Advantages of Wireshark as a Packet Analyzer:
In the past, network packet analyzers were costly and proprietary. However, the introduction of Wireshark has transformed the landscape by providing a free and open-source solution, making it one of the most powerful and accessible packet analyzers available today.
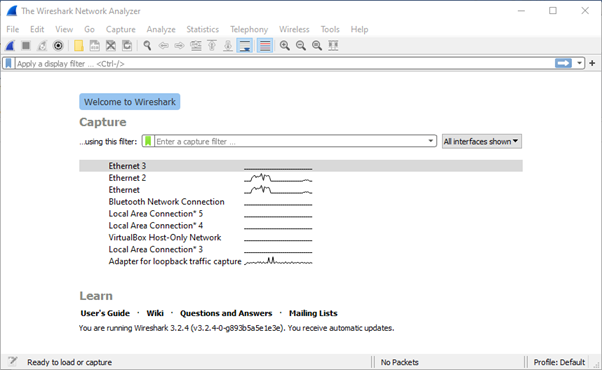
The above figure shows wireshark one of the best network security tool.
Three-Way Handshake:
A three-way handshake is a crucial process through which a computer establishes communication with a server. It involves three steps to initiate and confirm a connection. The first step occurs when the computer sends a Synchronization Packet (SYN) to the server, requesting to communicate. Upon receiving the request, the server evaluates whether to grant permission for the communication or not.
If the server approves the request, it responds with a Synchronization Acknowledgment packet (SYN-ACK), indicating that it is open and ready to accept incoming requests. The client, upon receiving the SYN-ACK, acknowledges the server's response by sending an Acknowledgment packet (ACK). This final step completes the three-way handshake, allowing both the server and the client to communicate openly, and a session is successfully established.
In this tutorial, we will analyze the three-way handshake process using Wireshark to gain insights into how the communication is initiated and confirmed between the computer and the server.
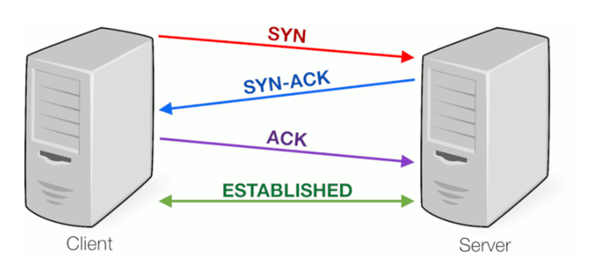
Capture Three-Way Handshake Using Wireshark;
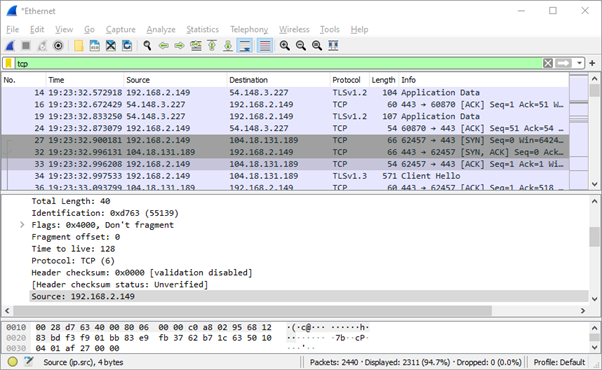
In Wireshark, a network packet analyzer, we can observe the three-way handshake by applying a filter for TCP (Transmission Control Protocol). TCP is a standardized set of rules facilitating communication between computers in a network. The three-way handshake is a critical process to establish communication between a computer and a server.
Upon examining the captured packets in the image, we notice the sequence of SYN, SYN-ACK (SYN, ACK), and ACK. Although the image might explain the order as SYN, ACK, and SYN-ACK (SYN, ACK), Wireshark might display it differently, possibly due to variations in times of receipt or other factors like time lag.
Examining the SYN (Synchronization) Packet:
This image is for reference:
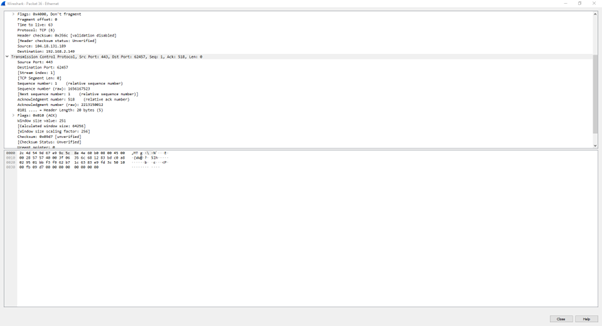
In the Wireshark capture, the second blue line displays a packet flagged as "SYN," indicating that it is a Synchronization Packet. This packet originates from the computer's communication endpoint, specifically from the Dynamic/Private port 62457. Ports serve as essential communication channels, enabling computers to both send and receive packets. The destination port in this packet is 443, which is a well-known port commonly used for HTTPS protocols, typically associated with secure web communication.
The source IP address identified in the packet is 192.168.2.149, which corresponds to the client's public IP address, while the destination IP address is 104.18.131.189, representing the server's IP address. The packet appears to have been transmitted without any immediate indication of being accepted or denied.
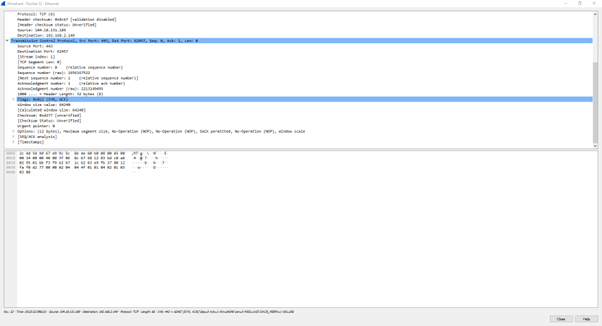
Examining the ACK (Acknowledgment) Packet:
Wireshark captures an ACK packet, as indicated by the Flags tab. This packet originates from the source port 62480 and is destined for port 80. The IP address of the sender or server is 104.18.131.189, while the recipient or client's IP address is 192.168.2.149.
.
The ACK packet signifies an acknowledgment of successful receipt or delivery of data. It is an essential part of the communication process, acknowledging the proper reception of previously transmitted packets.
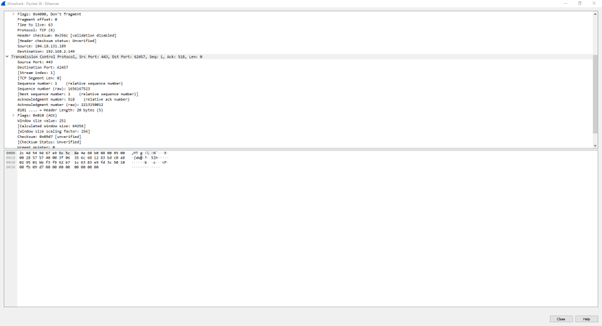
Examining the SYN-ACK Packet:
In the Wireshark capture, we observe a SYN-ACK packet, denoted by the Flags as (SYN-ACK). This packet is a critical part of the three-way handshake process. The packet is sent from port 453 and destined for port 62457. The source IP address, 104.18.131.189, belongs to the server, while the destination IP address, 192.168.2.149, corresponds to the client.
This SYN-ACK packet completes the three-way handshake, establishing a successful connection between the client and the web server. As a result, the client gains access to the website hosted on the server. However, the access is restricted to normal site privileges, meaning the client can view the website content but cannot modify any data or access sensitive user information. These restrictions are typically in place to ensure security and prevent unauthorized access to critical functionalities, which are usually reserved for privileged users like administrators.
Conclusion:
In conclusion, this tutorial lab provided valuable insights into the capabilities of Wireshark as a powerful network security tool. It allowed us to capture and analyze packets, gaining visibility into the incoming and outgoing traffic of data within the network.
Stay Tuned
The best articles, links, and news delivered once a week to your inbox.
