Six Best Tools for Malware Analysis - Static and Dynamic
Malware analysis is the process to determine the origin and the threat level of a malware sample. It's all about figuring out where bad software (malware) comes from and how dangerous it is. By studying the malware, experts can understand how it works and find ways to protect against it. It's like investigating a crime scene to see how much damage the malware has caused, what harm it can do, and what type of malware it is. By doing this, they can figure out how to stop it and keep computers safe.
Types of malware analysis:
There are two types of malware analysis methods used. One is static malware analysis and second is dynamic malware analysis.
Static malware analysis looks at the malware without actually using it. It's like looking at a picture of the malware to understand what it does. On the other hand, dynamic malware analysis is done in a safe computer setup, like inside a pretend computer. The malware is allowed to run, but any damage it does is undone, like going back in time to fix things. This way, experts can learn more about the malware and how to protect against it without risking real harm to computers
Static malware analysis:
Static malware analysis involves examining the malware's binary, which is like its DNA, to find out what it does. This is done by calculating a special signature for the file, sort of like a unique fingerprint. Then, the binary is put into a disassembler program (IDA) that converts it into a language that security experts can understand. By looking at this code, they can figure out what the malware is programmed to do and how it operates.
Dynamic Malware Analysis:
Dynamic malware analysis involves running the malware in a safe and isolated computer setup, like a pretend computer. While the malware runs, a security expert watches what it does to understand its behavior. This computer setup is closed off from the real world, so the malware can't harm other computers.
For more advanced dynamic analysis, a debugger is used. A debugger helps the expert figure out exactly how the malware works, like solving a puzzle. The main difference between static and dynamic analysis is that dynamic focuses on the malware's actions and behavior, while static analysis doesn't look at how the malware behaves when it runs.
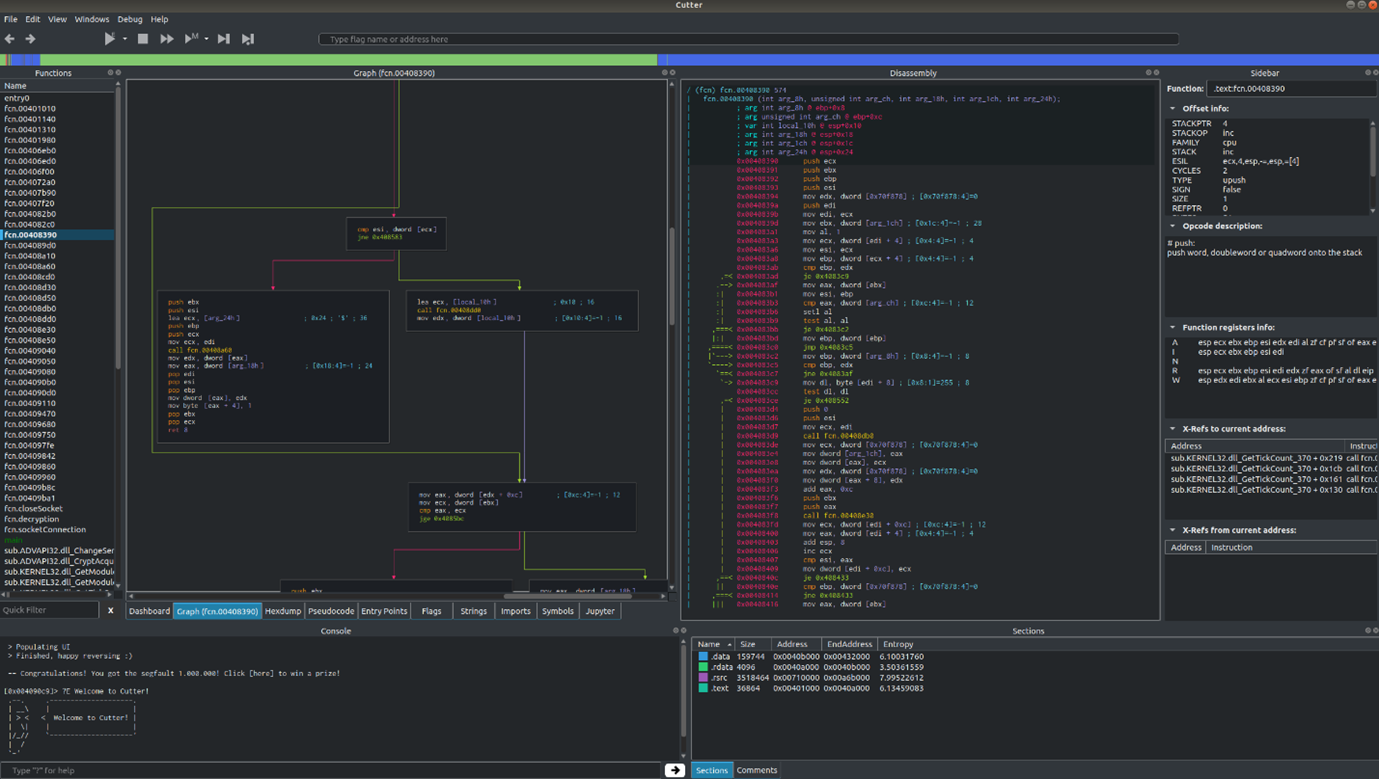
1) Cutter for Malware Analysis:
Cutter is an open-source Qt and C++ GUI that leverages the capabilities of radare2, an advanced reverse-engineering framework (explained in the next Figure). With regular updates every five weeks, this tool provides a wide array of features for reverse engineering purposes and is compatible with all major operating systems. Supporting both static and dynamic malware analysis, Cutter serves as a well-structured and enhanced version of radare2. It was first introduced to the public in March 2017.

2) Radare2 for Malware Analysis:
Radare2 is a comprehensive framework designed for reverse engineering malware and conducting binary code analysis. It was developed in February 2006 and serves as an open-source command line interface for malware analysis. Being widely recognized and utilized, Radare2 is among the most popular tools in the field of malware analysis, offering capabilities for both static and dynamic assessments.
3) Ghidra for Malware Analysis:
Ghidra is a powerful open-source software initially developed and utilized by the NSA. On March 5th, 2019, it was released as open-source, granting public access to its source code and enabling anyone to explore, experiment, and utilize the tool.
Regarded as one of the most exceptional reverse engineering tools available, Ghidra has gained high praise from security professionals. Its versatility is evident as it can be installed on various operating systems, including Windows, Mac, and Linux. Ghidra offers a range of features, such as disassembly, assembly, decompilation, graphing, and scripting, and users can even create their own customized versions and scripts for further flexibility.
4) Google Rapid Response (GRR) for Malware Analysis:
Google Rapid Response (GRR) is a valuable tool employed for analyzing malware traces on workstations. It enables response teams to perform diverse forensic tasks on machines, aiding in the investigation of potential infections. Additionally, GRR can collect malware samples for further examination using widely-used static or dynamic analysis tools.

5) YARA for Malware Analysis:
Yara is an open-source tool designed for malware analysis, operating on a rule-based system where users can define their own rules for analysis. With its powerful pattern matching capabilities, Yara can effectively identify and classify malware samples on any operating system. The tool enables signature-based detection of malware, functioning similarly to antivirus programs but offering a more detailed and advanced level of analysis. However, it should be noted that Yara is not beginner-friendly and requires some expertise in malware analysis to make the most of its features.

6) Cuckoo for Malware Analysis:
Cuckoo is a highly acclaimed open-source malware analysis tool widely used in the cybersecurity community. It facilitates advanced dynamic malware analysis by providing a virtual environment for testing suspicious files. When Cuckoo is installed, it sets up an additional virtual environment on the system. Users can upload potentially harmful files to the server, and Cuckoo executes them in the isolated environment, allowing observers to closely monitor the behavior of the malware.
A key feature of Cuckoo is its ability to capture screenshots, which enables the virtual environment to be restored to its original state after running the file, effectively preventing any further damage to the testing environment. This capability adds an extra layer of security to the analysis process.
Conclusion:
Through the use of these malware analysis tools, we gain valuable insights into the inner workings of malicious software, enabling us to better defend against attacks and protect our digital environments. With their open-source nature and continuous updates, these tools exemplify the collaborative and innovative spirit of the cybersecurity community.
Stay Tuned
The best articles, links, and news delivered once a week to your inbox.
