What is Cryptography? An Introduction to Secure Communication
In today's digital world, the importance of secure communication cannot be overstated. Whether it's transmitting sensitive information or safeguarding online transactions, cryptography plays a crucial role in ensuring data privacy and integrity. This cryptography tutorial serves as a comprehensive introduction. By the end of this tutorial, you will have a solid understanding of how cryptography works and how it can be applied to protect your data.
Definition and Purpose:
Cryptography is a term used in cyber security, computer science, and Information Technology. Cryptography is used to protect information and communication by using codes so only the people who the information is intended for can read it.
Brief History of Cryptography:
The idea of cryptographic messages dates back to ancient times Caesar Shift Cipher was invented during the Roman Empire and named after Julius Caesar it was used to encrypt military messages at that time.
Vigenère cipher:
It was invented in Italy in the 15th century by Giovan Battista Bellaso and one Italian Cryptologist this type of cryptography was actually a recreation of the Caesar Cipher but it was just made more complex by changing each letter with a different shift.
Modern cryptographic methods have evolved to enhance security and make it increasingly difficult for humans to decrypt encrypted data.
AES or Advanced Encryption Standard:
In 1998, the United States of America developed a cryptographic system that combines elements of the Caesar Cipher, Vigenère cipher, and XOR encryption. This system encodes data using binary digits (0s and 1s) and decodes it into ASCII characters, making it exceedingly challenging to decrypt manually or without the proper key.
Now let us examine some of the different types of cryptography:
The cryptography tools used are Caesar Cipher, Vigenère cipher, XOR Encryption, Homphonic Cipher, Substitution Cipher, File Hashing, and Transportation Cipher. Along with each cryptography are questions and secret messages meant to be decrypted. In this tutorial, all questions will be answered along with figures showing the findings found.
A rotation of three for a Caesar Cipher decryption:
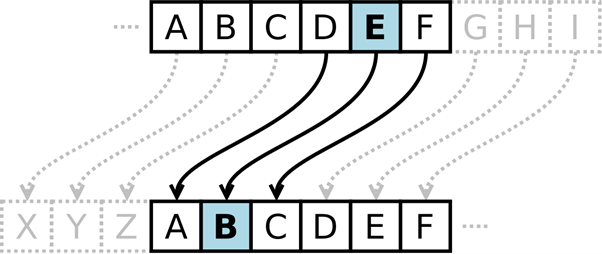
We will encrypt the below text:
“FI JEMXLJYP MR XLI WQEPP XLMRKW FIGEYWI MX MW MR XLIQ XLEX CSYV WXVIRKXL PMIW”
This encrypted message took a couple of hours to decode due to not having the key to decrypt it. After working for hours the number of rotations done in this code was 22 (rot22). The message states “BE FAITHFUL IN THE SMALL THINGS BECAUSE IT IS IN THEM THAT YOUR STRENGTH LIES” a quote by Mother Teresa.
Vigenère cipher grid used for deciphering or encrypting a Vigenère cipher:

The message to encipher is: MEETEIGHTWEDNESDAYBRINGPROPERMATERIALS
The keyword is: UTICACOLLEGEPIONEERS
To use the grid properly one needs to use the keyword first letter and associate it with the first letter of the message the U in this case with the M the top row is the M and the row on the left is the U the letter that meets in the middle of those two will be the new letter in this case G. The fully encrypted message is “GXMVEKUSEAKHCMGQECSJCGORRQDPCQGXTZWNPW”
To decipher this one would need the keyword and the graph and decipher it slowly one letter at a time to read the original message.
Cipher alphabet used in decrypting Homophonic cipher:
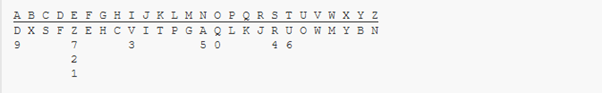
This type of cipher substitutes letters for other letters and requires a sort of alphabet to decode this alphabet. It can vary from person to person and there is no standard to follow but for this example, the alphabet below will be used to decipher the following.
AQ PZHDSB VR 40 J3SC 94 CQ51RUB
The encrypted message is a quote by William Shakespeare “NO LEGACY IS SO RICH AS HONESTY”. The alphabet shows how each letter is used one just needs to place the encrypted letters on the bottom row for example A and look at the top to see the original letter in this case A translates to N the numbers work the same this encryption is very easy to crack but becomes more difficult if one does not have the alphabet for decryption.
Conclusion
We may talk about many different methods but now moving on to the conclusion. In conclusion, cryptography is a time-tested method employed to secure communication. Its origins date back to ancient times and have been utilized by leaders and militaries throughout history. While cryptography has evolved, incorporating both older and newer methods, the underlying principles remain relevant. It is important to note that cryptography is not infallible, but its level of security depends on the specific techniques employed. Military and government entities extensively rely on cryptography to protect sensitive messages transmitted to soldiers and allies, safeguarding them from interception by adversaries. By employing various cryptographic methods, one can create robust encryption for messages, files, or even computer systems. However, it is crucial to acknowledge that with time and advanced equipment, even the most secure encryption can potentially be compromised.
Stay Tuned
The best articles, links, and news delivered once a week to your inbox.
