What is Social Engineering its 4 Types and how to Prevent Attacks?
Social engineering is a cyber-security term referring to the act of manipulating individuals to acquire sensitive data, finances, usernames, or passwords. Social engineers employ various tactics such as impersonating others or organizations to deceive their targets. These attacks can occur in person, through deceptive emails (phishing), or web spoofing.
The social engineer typically seeks out targets that may lack computer expertise and can be easily deceived, or they might engage in personal manipulation by posing as someone familiar to the target. Consequently, this method has been responsible for numerous successful hacks and compromised accounts, as unsuspecting individuals are caught off guard during these attempts.
4 Types of Social Engineering with Detail:
Although social engineering may have many types but here we will discuss about four major social attacks that you should prevent.
1) Phishing Email:
Phishing is a deceptive email attack designed to deceive individuals or groups into divulging private information, such as passwords, usernames, and even financial details. It may also involve tricking the target into downloading malware that can infect their entire system.
Another form of phishing, known as spear phishing, specifically targets individuals instead of a broad group.
Demonstration:
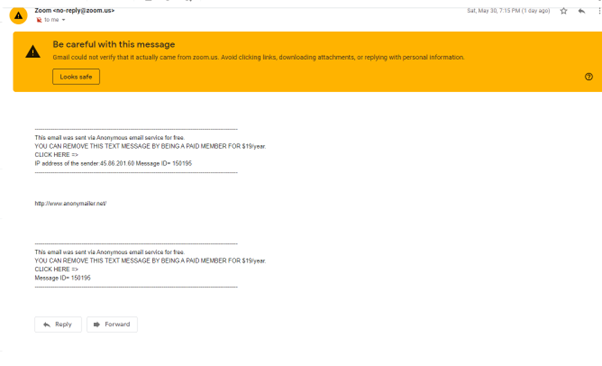
In the image above I sent a spoofed email to myself from anonymailer.com from the zoom team.
The email was sent but it went straight to spam and as shown in the image it warns that the email was not verified that it came from zoom.us. In the body I put the website anonymailer.net but the other information is not from me. The website offers a paid membership to remove this text it even gave the IP address from the computer it was sent from. Any beginner using this would either be ignored or reported and could be arrested for attempting to do anything wrong with this service. If the user decides to pay to protect themselves, they leave a trail that could be trailed back to them if they committed a crime. This shows that any person with a motive and the knowledge to attempt phishing would not go this route.
2) Fake IRS Webpage:
Proofpoint, a renowned security firm, uncovered a disturbing discovery of premade templates available on darknet forums. These templates are specifically designed for criminals to carry out phishing attacks, targeting users' login credentials and banking information. What's concerning is that these templates are crafted to closely mimic legitimate websites, making them almost indistinguishable from the real ones, even for experienced users. The criminals behind this scheme exploit the COVID-19 pandemic to take advantage of vulnerable individuals who are seeking help. Sadly, it is not uncommon for malicious actors to capitalize on panic and fear to pursue their illicit activities.
3) Spoofed Website Spam:
Spoofed website spam refers to a type of phishing attack where malicious actors create fake websites that closely mimic the appearance and functionality of legitimate websites. The purpose of these spoofed websites is to trick users into providing sensitive information, such as login credentials, personal details, or financial data.
Tricks to verify spoofed website spam:
Check the URL:
The first thing anyone would ever do in this case is hover over the link with the mouse and see the URL is the URL different or the same as the link provided.
Use Links to Verify:
In an instance where the link is provided and not encoded in a word such as “click here” the user is capable of using the links to verify if they are the same or if they are different if they are different that is already a clue to the link being fake.
Spelling Mistakes:
Users should also be vigilant for spelling mistakes and alternative symbols in URLs or website names. For instance, criminals might create fake websites that resemble popular platforms like "Twitter" but intentionally misspell it as "tw1tter," "tw1tt3r," "twitor," "twiter," "twἰttἐr," and so on.
Attractive Deals or Discounts:
Criminals often send emails containing attractive deals or discounts, luring recipients to click on provided links. To confirm the legitimacy of the offer, users should directly visit the official website of the company in question instead of clicking on the provided link. By doing so, they can verify whether the offer is genuinely being provided by the company. Alternatively, users can contact the company through legitimate means, such as their official phone number, to inquire about the offer's authenticity.
Check for HTTPS:
If a user has already clicked on a website link, the first step is to check if the website uses HTTPS. If it does not have HTTPS, it is generally advisable to leave the site immediately, although there are some exceptions where legitimate websites may not use HTTPS.
Financial Institutions Related Sites:
Many criminals tend to send spoofed spam sites that appear to be related to financial institutions, such as PayPal, eBay, banks, and government agencies like the IRS. If a website claims to offer financial services but lacks HTTPS, it is strongly advisable to avoid interacting with it altogether. HTTPS provides a layer of encryption and security that is essential for handling sensitive financial information. Therefore, any financial website without HTTPS should be treated with suspicion.
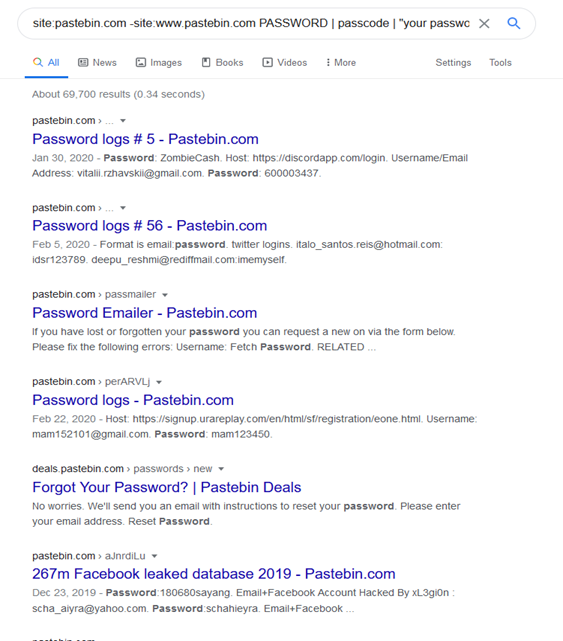
4) Google Search Hack:
Hackers tend to post on pastebin after the accounts have been compromised so searching pastebin instead of an organization made more sense for this search. The search used was site:pastebin.com -site:www.pastebin.com PASSWORD | passcode | "your password is".
Conclusion:
To conclude with the findings Social engineering is very dangerous with or without a computer. To avoid falling victim to various online threats, individuals need to practice good OPSEC (Operational Security), which involves taking measures to prevent mistakes and protect their privacy and security. It is crucial to raise awareness and educate all users about the importance of OPSEC to enhance their online safety and protect against cyber threats.
Stay Tuned
The best articles, links, and news delivered once a week to your inbox.