Why VPNs Are Essential for Cybersecurity

Regarding technology, it is often said that ‘the only certainty is uncertainty;’ hence, cybersecurity has become a priority for the masses. Over time, Virtual Private Networks (VPNs) have become one reliable weapon against cybercriminals. They offer immense numbers of benefits that increase the safety of organic networks and therefore are an establishment of any cybersecurity mechanism. The VPNs have become so crucial that in the first half of 2023 alone, VPN downloads surged to 130 million, highlighting their growing importance. This trend extends beyond individuals to businesses, with the global VPN market valued at $45 billion and projected to reach $137.7 billion by 2030, growing at over 15% annually.
On the other hand, cybercriminal activities are also on the rise. In 2022, the FBI received a record 808,297 complaints, resulting in $10.3 billion in losses. Common cybercrimes like phishing, data breaches, and identity theft underscore the importance of VPNs. Yet, despite the risks, 61% of people either don't use VPNs or are unaware of their benefits due to perceived complexities and costs. As security threats evolve, the shift towards advanced platforms highlights the need for ongoing technological innovation to combat new threats effectively.
This article seeks to explore the common cyber attacks and parameters or methods that entail the use of VPNs for security, including security against data breaches, secure transmission of information, security against tracking, and psychological security.
Let’s start.
9 Common Cyber Attacks That An Individual/Organization Faces Without a VPN
Organizations and individuals can face cyber threats without VPN, leading to significant security breaches. Understanding these threats is crucial for implementing effective cybersecurity measures. Here are some prevalent types of cyberattacks:
- Malware Infections
○ Prevalence: 33%
○ Description: Malicious software designed to damage, disrupt, or gain unauthorized access to systems.
- Zero-day Exploits and Advanced Persistent Threats (APTs)
○ Prevalence: 29%
○ Description: Attacks targeting unknown vulnerabilities and long-term, targeted data theft.
- Distributed Denial-of-Service (DDoS) Attacks
○ Prevalence: 24%
○ Description: Overwhelming a network with traffic to render it unavailable.
- Man-in-the-Middle (MitM) Attacks
○ Prevalence: 22%
○ Description: Intercepting and altering communications between two parties.
- Privilege Escalation Attacks
○ Prevalence: 20%
○ Description: Exploiting flaws to gain elevated access to restricted areas or data.
- Data Exfiltration Attacks
○ Prevalence: 18%
○ Description: Unauthorized transfer of data from an organization to an external location.
- Brute Force Attacks
○ Prevalence: 11%
○ Description: Attempting numerous password combinations to gain unauthorized access.
- Cross-site Scripting (XSS)
○ Prevalence: 11%
○ Description: Injecting malicious scripts into web pages viewed by other users.
- Remote Code Execution (RCE)
○ Prevalence: 9%
○ Description: Executing arbitrary code on a targeted system to compromise it.
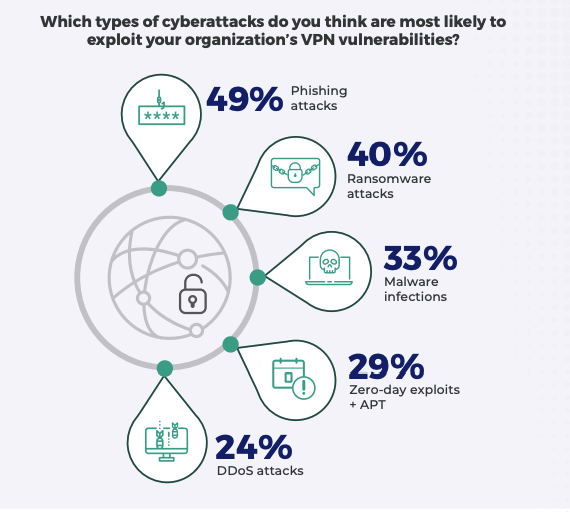
Concerns about cyberattacks exploiting VPN vulnerabilities (ZScaler)
VPNs serve as a crucial defense mechanism against various cyberattacks by encrypting data, masking IP addresses, and providing secure connections.
Key Benefits of Using a VPN for Cybersecurity
Protection Against Data Breaches
Security threats have rapidly increased in recent years, and hackers always look forward to finding new ways to access personal details. VPN is an Internet security service that enables clients to use the Internet to connect to a private network. VPNs provide security to users as they use apps and web properties over the Internet by ensuring this process is unobserved.
The security offered by VPNs is invaluable for businesses. Many organizations manage large volumes of confidential data, including customer information, financial records, and trade secrets. The average cost of a data breach for businesses worldwide was approximately $4.24 million in 2023, marking a significant increase from previous years (source). Beyond financial losses, data breaches can lead to reputational damage, regulatory non-compliance, and substantial penalties.
A VPN provides a secure method for connecting remote offices, enabling employees to access company resources without compromising security. This capability is critical for controlling user access to sensitive data and ensuring that valuable resources remain protected from unauthorized access.
Encryption of Sensitive Information
The most crucial feature a VPN is designed to perform is ensuring your traffic is secure. Encryption is a technique that makes data complex to the extent that only those who have the required keys can understand the encrypted data. VPNs implement highly secure avenues to connect through the implementation of IPsec or SSL/TLS encryption protocols. This makes it possible that even if communications occur through data transmission, the data cannot be understood by anyone other than the intended recipient.
Prevention of Tracking
In today's digital age, online tracking has become pervasive. Advertisers, websites, and even government agencies track your online activities to gather information about your preferences, behaviors, and personal information. This tracking not only infringes on your privacy but also makes you vulnerable to targeted attacks and identity theft.
VPNs provide a solution to stop third-party individuals from tracking your online behavior. A VPN essentially alters the routing of your internet connection so that your IP address is concealed and your geographical location is changed. This makes it difficult for websites and advertisers to track your online behavior and collect your data. Additionally, many VPNs offer features such as ad-blocking and anti-tracking, further enhancing your online privacy and security.
Improved Online Privacy
VPNs supplement strength and afford protection against identity theft. Through encryption, VPNs hinder hackers from obtaining sensitive personal information like credit card details and social security numbers.
Thus, a VPN shields your information from being monitored by websites, applications, and even your ISP. This ensures that your personal details do not leak into the wrong hands.
Enhanced Security for VoIP Services
VPNs are secure connections for VoIP services such as Skype and Zoom. This means that your voice and video calls will be totally secure, and the transmission will be protected from listening in. It also means that your use of the services cannot be monitored by other parties, thus maintaining your privacy when making the calls.
Boosted Confidence in Online Transactions
In online shopping, using a VPN can limit the exposure of the buyers’ financial details to hackers. This is especially true when connecting to public wireless networks that are open for everyone to access.
How VPNs Help with Access Control
Another critical application of VPNs is as a means of access control. VPNs mainly enhance access control solutions, whereby only accredited users can view specific resources. Imagine there are two servers in Acme Co.'s office building: Server A and Server B If Bob wants to Print a document stored on Server A at the office using the office printer, Bob will need to connect to the appropriate network. If, on the other hand, Acme Co. uses WPA and VPN, Bob will have to log in to VPN A to access Server A and VPN B to Server B. The virtual network system within the company insulates users; therefore, everyone does not have equal access to the data but only according
Selecting the Appropriate VPN for Cybersecurity
When selecting a VPN for cybersecurity purposes, consider the following factors:
1. Strong Encryption Protocols
Choose a VPN that utilizes the best encryption protocols, such as OpenVPN or WireGuard, to ensure the highest level of data security.
2. No-logs Policy
Choose a VPN provider with a no-logging policy. This policy ensures that your internet activities are not recorded in any way.
3. Reliable Performance
Ensure the VPN offers high connection speeds, as slow speeds are a big turn-off and may lead to the last meeting on the VPN service.
4. Multi-platform Support
Select a VPN that allows multiple operating systems and gadgets, covering all your gadgets.
5. Customer Support
It is vital to have proper customer support in case some problems with a product arise or to set it up.
Conclusion
VPNs are a crucial asset for protecting organizations and individuals from cyber threats. They offer protection against hacking, secure data transmission, and a shield against tracking—all essential in our rapidly digitizing world. Additionally, using a VPN can lead to positive psychological outcomes, such as reduced stress, improved concentration, and a greater sense of control.
In summary, VPNs provide:
● Robust protection against data breaches by encrypting data and ensuring secure transmission.
● Enhanced privacy by preventing online tracking and shielding personal information.
● Secure communication channels for VoIP services and online transactions.
● Effective access control to ensure only authorized users access specific resources.
Adopting a VPN is a proactive step toward safeguarding your online identity as technology advances. A VPN is an indispensable tool for those seeking enhanced protection and for businesses aiming to secure their valuable data. By setting up a VPN security protocol, you can improve and secure your online navigation, reducing the worry of privacy interference or data theft.
Take the step today to protect your digital life. Choose a reliable VPN service that meets your needs and enjoy peace of mind with enhanced online security.
Interested in VPN Services?
If you're looking for reliable VPN services to enhance your online security, check out our detailed reviews:
- AdGuard: Visit AdGuard
- Surfshark: Visit Surfshark
These reviews will help you choose the best VPN service that meets your needs and enjoy peace of mind with enhanced online security.
Reviews:
-
Choosing Your Shield: A Comprehensive Review of AdGuard's Personal and Family Plans
Explore the features and benefits of AdGuard's personal and family plans for comprehensive online protection. -
Choosing Your VPN: A Detailed Comparison of AdGuard and Surfshark for Online Protection
Compare AdGuard and Surfshark VPNs to find the best option for your online security needs. - What is Surfshark Beyond VPN? Exploring the Full Arsenal for Ultimate Online Protection
Learn how Surfshark provides a holistic approach to online security and privacy, ensuring comprehensive protection for your digital life.
References
● https://purplesec.us/resources/cyber-security-statistics/
● https://www.statista.com/statistics/542817/worldwide-virtual-private-network-market/
● https://www.fbi.gov/contact-us/field-offices/sanfrancisco/news/fbi-releases-internet-crime-report
● https://www.techopedia.com/vpn/vpn-statistics#:~:text=References-,VPN%20Statistics%20Highlights,(Atlas%20VPN%2C%202023).
● https://nordvpn.com/blog/what-is-openvpn/
● https://cybernews.com/what-is-vpn/wireguard-protocol/
● https://www.zscaler.com/resources/industry-reports/2023-vpn-risk-report.pdf
● https://www.ibm.com/reports/data-breach
● https://www.cloudflare.com/learning/network-layer/what-is-ipsec/
Stay Tuned
The best articles, links, and news delivered once a week to your inbox.
